Basic knowledge of authentication system
A authentication system is a system that checks the legitimacy of the user and permits or refuses access.In this series, we will discuss the authentication system in the sixth series.Recently, various incidents and accidents have occurred in connection with authentication.In information (cyber) security, it is important to understand the authentication, one of the most basic elements, and to manage, operate and use appropriately.The first section describes the role of authentication and the threat to authentication.
Lottery
1st: Think of authentication
1.Position of "authentication" in computers and services
The following three are particularly important and basic elements in considering the security of computers and network services.
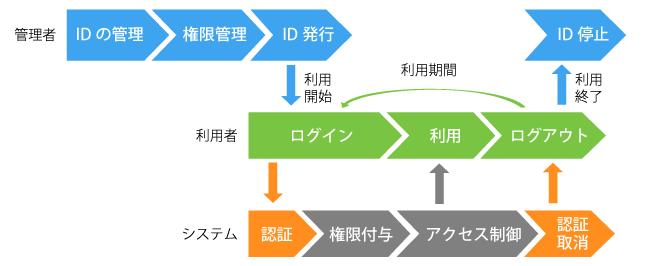
In other words, the user ID is issued based on who needs to permit and what use is determined, and the functions (authority) available in that ID are determined.The system determines by authentication that the user who has entered the ID is issued by the ID, and if the identity can be verified, the permissions on a predetermined system will be granted (approved).The operations actually performed by the user are allowed within the permissions given here, and other operations are prohibited.This is called access control (Fig. 1).
図1:ID管理、認証・認可、アクセス制御の関係If the user does not need to use the system, it is necessary to disable the issued ID and not be used thereafter.If the content or purpose to use changes, you must change the authority to give accordingly.Otherwise, you will forgive users for unnecessary or inappropriate access.Authentication and access control are mechanically performed based on the ID and the permissions given, so if the management is insufficient, the security foundation will collapse.
Authentication is a step to verify the user's identity.Inside the system, the user is managed by the ID.If you use a formal ID, you can unconditionally exercise the authority given to that ID.Therefore, the first barrier is ...
>>第1回 第1章の続きを読む(PDFダウンロード)
2.Threat to authentication
The magnitude of threats to authentication depends on the functions and information provided by the system.The greater the profit gained by breaking the authentication and using the system fraudulently, the greater the threat.For example, online banking -like services have a direct and financial benefit, so you must prevent attacks from a criminal organization like a criminal organization.Similarly, even on online sales websites, if the benefits you get, you will always be exposed to various attacks.
Even if you do not get money directly, the information gained from that computer or service may be valuable.In systems that include personal information, especially credit card information, etc., it is necessary to pay attention to attacks aimed at such information.
Even systems that cannot access directly from the Internet cannot be careless.In recent years, the number of targeted attacks that send malware (unauthorized programs such as computer virus) is increasing to steal information (Figure 2).Many of the malware used for such an attack ...
>>第1回 第2章の続きを読む(PDFダウンロード)
2nd: Basics of authentication
Last time, I explained the role of authentication and the threat to authentication.This time, I will explain the basic concept of authentication and authentication using the most common authentication method and password.
1.Elements for authentication
As mentioned in the first time, authentication is a step to confirm that the person you are trying to access is definitely a formal person (or equipment or services).For this reason, the authentication system requires the access to the accessories to prove the legitimacy at the same time as the user identification ID.This information is called authentication element.
図1:利用者識別と正当性の確認For example, PIN and password are one of the authentication factors.These are based on the knowledge based on the knowledge that only legitimate users can know.On the other hand, authentication using a tele -certificate, smart card, one -time password occurring machine, etc. checks the legitimacy based on the assumption that the user has it (owned).Biological authentication that uses patterns such as fingerprints, palms, veins, and irises is also assumed to be owned.These are targeted for humans, so you can check your personality more strictly.
However, these authentication elements are not perfect.Knowledge can be a third party due to leaks and guess.In addition, the possibility of theft and counterfeiting is also attached to what you own.
The authentication system determines whether to allow access using these authentication factors.However, to prevent fraudulent use ...
>>第2回 第1章の続きを読む(PDFダウンロード)
2.Certification by PIN and password
Passwords (passphras) and PIN are the most popular authentications based on knowledge.Password authentication is used in most systems and services and is used in all aspects of work and life.The main reason is that the password authentication mechanism is standard implemented in most computer OS and development frameworks, so it can be implemented without additional costs.In the password or password authentication, the user is authenticated on the following assumptions.
Therefore, if one of these assumptions is broken, the safety of password authentication will be impaired.Let's consider the situation where the premise 1 has collapsed.
These are all typical examples.In this way, if the password secret is impaired, the safety of authentication will greatly decrease.In particular, if the user is not aware of this situation, the risk of unauthorized use of the system will increase.On the other hand, if the user has noticed, it is possible to avoid the risk for the time being by changing the password.Also, if you change your password regularly, you will be able to reduce the risk if you do not notice it.
However, the assumption 2 is a little complicated.Here are some cases where passwords and passwords can be caused by others.
...
>>第2回 第2章の続きを読む(PDFダウンロード)
3rd: Various threats to password authentication
Last time, we introduced the basic concept of authentication and authentication using PIN and password.This time, I will explain the serious threats to password authentication and the countermeasures.
1.Attack on passwords, not just from the front entrance
The attack on the authentication function itself, which was introduced last time, is a threat to the outer entrance of the authentication.But that is not the only threat to authentication.No matter how complicated the password is set, if the password stored in the system is stolen, it doesn't make any sense.
通常、システムに保存されているパスワードには、外部からアクセスできません。外部どころか、システム内部でも管理者権限がないとアクセスできないのが普通です。しかし、こうした保護をバイパスできる裏口があります。それが脆弱性です。
Vulnerabilities are caused by defects in systems (such as software bugs or design insufficient consideration) that can be invalidated or avoided.Serious things can avoid authentication to invade the system by abusing them, or access data that cannot be accessed from outside.
Generally, the password of the user is stored in the form of files and databases in the system, and general access is prohibited by access control.However, abusing vulnerabilities can provide external access (Fig. 1).
図1:脆弱性を悪用した攻撃こうした手段で攻撃者が利用者のパスワードを入手してしまえば、もはやそのログインを防ぐ手立てはありません。このため、万一の漏えいに備えて、...
>>第3回 第1章の続きを読む(PDFダウンロード)
2.Attack by password list
Password outflow does not necessarily mean that the leakage system is damaged.In particular, the service provided on the Internet often uses email addresses in the ID, and many users use the same combination of the same email address and password in multiple services.It is.Therefore, if a combination of ID and password is leaked from one service, it may abuse it and may cause infringement in other services.
実際、IDとパスワードの組み合わせリストは闇サイトなどで流通しており、近年それらを使ったリスト型攻撃が多数確認されています。リスト型攻撃では、1つのIDに対して試行は1回のみなので、...
>>第3回 第2章の続きを読む(PDFダウンロード)
4th: Various authentication method 1
Last time, we introduced a serious threat to password authentication and its countermeasures.From this time, I will explain the main authentication method other than password authentication.
1.Certification by one -time password
One of the major premise of password authentication is that the secret, that is, the password may not be leaked to others (see the second).However, a variety of measures are required for that, not only puts the burden on the user, but also the risk of leakage even under sufficient management.What was considered is a one -time password (OTP), a so -called disposable password.As the name implies, the one -time password is invalid in one use.For this reason, it is necessary to use different passwords each time, and even if there is a peeping or eavesdropping in the case of authentication, it will not be reused (Fig. 1).
図1:ワンタイムパスワードThe early one -time password was used by the user and used in order by the user of the password created by the system.The user and the system share the password list, enabling authentication.In other words, one -time password is not a knowledge, but a certification based on the property of a list.However, the number of passwords that can be retained is limited, and it is difficult to store lists with many passwords.That's where the one -time password machine (sometimes called a token).
The user enters the password displayed by the generator (in many cases) displayed by the generator when performing password authentication.The password is different for each authentication.Depending on the method, the displayed password is invalidated in a certain time, so even if it leaks unused, it cannot be used later.In addition, there is no need to reissue after using up like a list, and it can be used unlimitedly within the expiration date.
さて、ここで疑問が生じます。発生するパスワードは、...
>>第4回 第1章の続きを読む(PDFダウンロード)
2.Cryptographic authentication and smart card
There is also a way to use encryption technology more directly for authentication.The basics of modern ciphers are that, as mentioned earlier, the decryption (the same result) cannot be performed without accompanying, and the accompaniment cannot be guessed from the encryption column.Therefore, if the system can verify whether the user has an officially distributed accompaniment, the authentication will be established.In this method, we also authenticate on the assumption that the user owns the unique encryption information.
To put it simply, if the user encrypts a specific data and sends it to the system, and the system can be decrypted with the same accompaniment, it can be confirmed that the user has the accompaniment.However, doing so can cause problems.If the same data is encrypted with the same encryption, the result is always the same.In other words, if you can steal encrypted data, you can reuse it and break through the authentication.This is called a replay attack.In order to prevent replay attacks, the encrypted data must be changed every time.
In other words, if the accompaniment is the same, it is necessary to change the encryption data every time, so it is a problem to share the data between the user and the system side.It is the communication method called the challenge and response system (Fig. 5).
図5:チャレンジ・レスポンス方式チャレンジ・レスポンス方式では、...
>>第4回 第2章の続きを読む(PDFダウンロード)
5th: Various authentication method 2
Last time, we introduced one -time passwords and cryptographic authentication as a certification method other than general passwords.This time, I will continue to explain the various authentication methods.
1.Cryptography and key protection
As described earlier, cryptographic authentication confirms legitimacy by proof that you own a unique encryption key.For this reason, protection of unique keys is important.To protect the unique key more firmly, use a dedicated hardware for key storage, such as a smart card or a dedicated USB key.These are called hardware tokens or hardware containers (Fig. 1).On the other hand, key protection by encryption using a password is a software token or software container.
図1:暗号鍵格納用ハードウェアの例With these dedicated hardware, the user's unique key is stored in the tip and cannot be taken out.The hardware is equipped with a CPU, enabling a small amount of data encryption and decryption.At the time of authentication, ask this hardware to encrypt the challenge, receive the result and send it back to the server side.You can now authenticate directly without calculating the key (Fig. 2).These hardware is not only provided with the prime resistance mentioned earlier, but also can be locked by password, so it is protected for loss and theft.
図2:スマートカードの仕組み一方、認証サーバ側では、...
>>第5回 第1章の続きを読む(PDFダウンロード)
2.Biometrics authentication
The ultimate of authentication by ownership is biometric authentication.The authentication method so far can be used not only for human -to -human systems, but also between systems and various devices and services.On the other hand, biometric authentication is a method specializing in human authentication.It is used as a authentication element is the unique characteristic of the human body.
The most popular is fingerprint authentication (Fig. 5).Fingerprints are representatives of physical characteristics that can identify individuals, as they are also used for criminal investigations.The same thing is a palm crest.However, simple fingerprint authentication accompanies the danger of counterfeiting.It is relatively easy to collect and forge someone's fingerprint.In fact, there are some studies that you can break through fingerprint authentication by taking fingerprint molds and using gummy of sweets to make fake fingerprints.To prevent such counterfeiting, you must use another means to confirm that it is a living human finger.
図5:PC用指紋認証装置の例より偽造が困難な方法として、皮膚の下にある血管(静脈)のパターンを検知して認証する方法があり、銀行のATMなどで多用されています。それ以外にも、...
>>第5回 第2章の続きを読む(PDFダウンロード)
3.Multi -element authentication
As we have seen, each authentication method has its own advantages and weaknesses.In particular, the weaknesses are largely due to the characteristics of the method, and if you try to cover them forcibly, you will be more likely to decrease convenience and increase costs.
Therefore, in order to cover the weaknesses of a certain authentication method, multi -factor authentication is used in combination of different authentication methods with different characteristics.For example, recent online banking sites often use one -time passwords in addition to regular passwords.This covers the weaknesses of password leakage and estimation.On the other hand, using a normal password to protect the stolen and unauthorized use of a one -time password.In this way, combining each other's weaknesses is the basis of multiple element authentication.
組み合わせにおいては、第1回で述べた、知識ベースの認証要素と所有ベースの認証要素を組み合わせるものが最も有効です。それぞれの持つ特性が異なるため、互いの弱点をカバーしやすいからです。知識ベースの要素を複数組み合わせた場合、記憶の手間が増えます。一方、所有ベースの組み合わせは、複数の機器を持ち歩くなど、かさばる場合があります。例外があるとすれば、...
>>第5回 第3章の続きを読む(PDFダウンロード)
6th: Complied authentication method
Last time, I explained about cryptographic authentication, biometric authentication, and multi -factor authentication.This time, we will explain the complementary authentication method used to combine with the main authentication method and confirm related operations.
1.Certification by secret questions
The secret question is a commonly used method as a means of confirmation of password recovery and risk -based authentication (described later).The questions that have been decided in advance and the answer are set as a set, and the person's personality is authenticated by confirming that the answer is correct.Users can select questions that can be answered again as a memory that you do not need to remember again.Some users, including questions, can be registered, but in many cases the system is selected from the options prepared in advance.This also makes sense to prevent the user from setting an incorrectly unpleasant question.
質問から誘導される回答は、秘密性を保証できるものであることが必要です。例えば「電話番号は?」「自動車のナンバーは?」などの質問は、一般に回答の秘密性が低いために、好ましくないといえます。一方、「初めて飼ったペットの名は?」「母の旧姓は?」といった質問は、...
>>第6回 第1章の続きを読む(PDFダウンロード)
2.Confirmation and approval by email, telephone, SMS, etc.
It is often used to send a confirmation email to the registered e -mail address when registering an ID or changing important matters.This is to make it possible for formal users to recognize the change operation by spoofing ID registration and unauthorized access.Introducing confirmation by e -mail, telephone / SMS and authentication examples.
In many cases, the email has an approval URL, and the operation is not completed unless you access it and perform the approval operation (Fig. 1).
図1:メールによる確認・認証例あらかじめ登録された電話番号に、音声やショートメッセージ(SMS)などでコードを送り、それを入力させて確認する方法もよく使用されます。これはメールに比べ、...
>>第6回 第2章の続きを読む(PDFダウンロード)
3.Recovery of authentication elements
If you forget your password or lose your card, you will need recovery.In these recovery, it is necessary to reset the authentication element itself.In the past, the system administrator has been performed after a system administrator receiving a request from the user, confirming his identity.However, in recent years, recovery has been increasingly performed by self -service to reduce the load on administrators.
If the user himself performs operations such as resetting when forgot the password, disabling cards or one -time password generators, or registration of use at the time of reissue, it is a legitimate user.The problem is how to check and authenticate.In this case, the original authentication method cannot be used, so some alternative means are required.
最もよく使われている方法が、図1のメールを使う方法です。パスワードの再設定を要求する際、まず登録済みのメールアドレスの入力を促します。入力されたメールアドレスが登録済みのものと一致すれば、そのアドレスにメールを送ります。もし一致しなかった場合でも、特にエラーを出したりはしません。これは、入力を繰り返してメールアドレスを特定されるのを防ぐためです。送られたメールには、パスワード再設定用のURLが記載されており、利用者はそこにアクセスしてパスワードを再設定します。ここでは、利用者側でメールの秘密が保たれていることを前提としています。近年、メールサーバ間での通信が暗号化されることも多くなり、メールの盗聴の可能性は低くなりました。しかし、...
>>第6回 第3章の続きを読む(PDFダウンロード)
4.Risk -based authentication and behavior pattern authentication
Even if the authentication is successful, it may calculate the possibility of spoofing, not the original user, and will automatically demand additional authentication if it is high.This is called risk -based authentication.Many credit card companies check the use in time, which is considered difficult to move, based on the time intervals of cards and the area used.These checks are also possible in system authentication.In the risk -based authentication system, this is performed using the various attributes of the authentication (Fig. 3).The attributes used are
・クライアントのIPアドレス
Based on information such as the assignment area of IP addresses and ISPs, check the use of geographical gaps and use in countries that are different from usual.
・クライアントの利用環境
In the case of web -based authentication, check the browser information (user agent information) at the time of access and the application information used, and check the use from different browsers, applications, and OS environments.
・クライアントのアクセス時刻
Check if the time for the client to access the authentication system is very different from usual
といったものが考えられます。もちろん、たまたま利用者がそのようなアクセスを行った可能性もあり、こうしたチェックは、あくまで目安に過ぎません。そこで、利用者をより厳密に確認するために、...
>>第6回 第4章の続きを読む(PDFダウンロード)
7th: Single Sign -on and Federation
Last time, I explained the complementary authentication method used in combination with the main authentication method.This time, we will explain the single sign -on that enables multiple systems access to multiple systems with a single authentication, and federation, which allows ID and authentication interacting between services that are managed and operated.
1.Single sign -on and its mechanism
Various systems are running in organizations such as companies.These are not all started to operate at the same time, and many have been added later as needed.It is only natural that corporate systems that handle important information require certain ID management, authentication and access control.However, if these mechanisms are implemented for each system, management will be complicated, and login will be required for each system, which will be inconvenient for the use side.In recent years, as the changes in the business environment have been severe, the information system has been forced to respond quickly to the environment, and new systems have been added and frequent.In such a situation, if ID management and authentication are performed individually, the operation of the system will not be established.
A measure to solve these problems is the unification of ID management and authentication by single sign -on.In a single sign -on environment, users can move between the systems freely by receiving only once.The system allows user access in cooperation with the authentication system that provides a single sign -on, rather than performing authentication or ID management.Figure 1 shows the flow of single sign -on.
図1:シングル・サインオンの流れWhen the user accesses each system, the system sends the user to the authentication system once and is authenticated there.Once the authentication is completed, the user is returned to the system as well -authenticated, and the system gives the ID determined by the ID and permits access.The authentication system determines whether the sent user has been authenticated, and if it is not authenticated, displays the authentication screen again and receives authentication.With such a mechanism, users will be able to log out or go back and forth in multiple systems until a certain period of time has passed.
旧来のクライアント・サーバ型のシステムでは、こうしたシングル・サインオンの実現には、使用する認証システム製品(シングル・サインオン製品)に固有のプラグインなどが必要となり、製品への依存が強くなりがちでした。一方、近年主流となっているWebアプリケーション主体のシステムでは、...
>>第7回 第1章の続きを読む(PDFダウンロード)
2.ID / authentication collaboration (federation) and cloud
By the way, expanding single -signions from corporate systems (so -called on -premises system) to cloud services will provide authentication between services with different operations. As a result, there is a problem of how to keep such a trusting relationship between different subjects. Naturally, companies need to consider the security risks of all cloud services. In terms of ID and authentication management, service providers also have the risk of accepting external ID management and authentication results. The risks of these businesses may spread to all users due to the characteristics of multiple users (corporate users = tenants) using the service base (this is called multi -tenant). Of course, in multi -tenant systems, the responsibility of the user's user management and passwords is often the case on the user. For this reason, the cloud business operators logically the system environment of each user so that the risk caused by the management deficiencies of the user does not spread to the management system and service base of other users and business operators. We are taking measures tool. The acceptance of the user's authentication results is based on such a quarantine.
In this way, the id and authentication collaboration (Federation) has expanded the concept of accepting the ID and authentication management of others (Fig. 3).If different companies and businesses can accept the other party's ID and authentication results, the convenience of users will be increased at a stretch.Of course, for this, in addition to the isolation of the user environment described above, it is necessary to meet the company's demands of the company's ID management and authentication of the other businesses and corporate businesses and companies.
図3:企業間フェデレーション企業同士のフェデレーションには、例えばグループ企業間、取引先、合併時などにおける、システム機能の相互または一方的な利用が必要とされるときに、ID管理や認証の統合なしに利用できるというメリットがあります。企業間のフェデレーションでは、ビジネス上重要な情報を扱うことが多いため、...
>>第7回 第2章の続きを読む(PDFダウンロード)
8th: Operation and management of authentication system
Last time, I explained about single sign -on and federation.This is the last episode, and here are some points to keep in mind when managing and managing the authentication systems mentioned so far.
1.The importance of ID management
The management of the user ID and the management of authentication are closely related.Giving an ID, that is, giving a service account to the user is to allow users to use the service.If it is a corporate business system, the management of these users will be closely related to HR.For this reason, the ID management process is generally set in accordance with internal regulations.Companies create an account required for business, grant IDs, and allow access only in the necessary information and functions.
また、特に人事異動に伴うアカウントやその権限の変更は、確実に行われる必要があります。不要になったアカウントや権限を放置すれば、思わぬ事故につながりかねません。とりわけ、退職者のアカウントは...
>>第8回 第1章の続きを読む(PDFダウンロード)
2.Manage password
Management of authentication elements such as password is basically the responsibility of the user.For this reason, it is necessary to inform users in an easy -to -understand manner and understand the appropriate criteria for password settings and the precautions for handling (such as not writing and putting it on sticky notes).On the other hand, the complexity of the password (number of characters, characters, etc.) can be checked on the system side so that it does not accept any standards.In Windows and other OSs, the use of a vulnerable password can be prevented to some extent by using the function (standard equipment) that enforces the password policy (standard equipment).The same is true for the change frequency, and regular changes can be forced by the system.
However, as described in the password authentication item (2nd), excessive enforcement may be a problem.Too long password requirements can be a risk of using vulnerable passwords, such as repeating simple words.There is a possibility that a frequent change request will be taken in a simple way, such as simple letters and order replacements (Fig. 2).
図2:過度なパスワードポリシーの弊害Such a password will ruin your password policy.Also, it is very difficult to check all these straightforward changes in the system.
一方、8文字程度のパスワードでも、適切に作れば、...
>>第8回 第2章の続きを読む(PDFダウンロード)
3.Authentication system log
The important thing when operating a authentication system is log management.Success or failure of authentication is required to be recorded.Not only failure but also success is needed because it is very important to know who logged in to the system.If you need to track the system usage status for any reason, you can be able to aggregate the login status with a specific ID and it will be possible.Understanding the usage of information system is one of the important tasks for the IT department, so the authentication log is useful for its aggregation and analysis.
From a security point of view, there is a possibility that a sign of fraud is found in the system usage.Outside work hours, especially at midnight and holidays, and remote access, it is possible to be able to reach the monitoring, causing a fraudulent hotbed, or a problem in labor management.For this reason, regular aggregation and check of authentication logs have significant meaning.In Windows, the acquisition of authentication success log is invalid in standard, so it is recommended that you enable it for a particularly important server, such as a domain controller or file server (change is the local security policy.It is performed in the auditing group policy).
一方、認証失敗ログのチェックでは、...
>>第8回 第3章の続きを読む(PDFダウンロード)
4.Correspondence to authentication logs and security incidents
As mentioned above, the log of the authentication system is a clue to find fraud and attacks.On the other hand, security incidents (accidents) may occur, such as leakage of information or malware infection inside the system.At this time, if you can find and scrutinize the authentication log, you can find an unusual login or an unauthorized access to an administrator account, which will help you elucidate the cause of the incident.
For this reason, if a security incident occurs, the log of the suspected system must be preserved as soon as possible.Even if it is not destroyed, it may be erased by rotation to ensure capacity.In particular, the Internet public service, which has many users, tends to shorten the log storage period.If the timing of conservation is delayed, you will lose great clues.
また近年、政府機関、重要インフラ、基幹産業などをピンポイントで狙った、いわゆる標的型攻撃が...
>>第8回 第4章の続きを読む(PDFダウンロード)


![10th generation Core i5 equipped 9.5h drive mobile notebook is on sale at 50,000 yen level [Cool by Evo Book] 10th generation Core i5 equipped 9.5h drive mobile notebook is on sale at 50,000 yen level [Cool by Evo Book]](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/9/4a18d0792cae58836b71b9f591325261_0.jpeg)



![[Amazon time sale in progress! ] 64GB microSD card of 1,266 yen and wireless earphone with noise canceling function of 52% off, etc. [Amazon time sale in progress! ] 64GB microSD card of 1,266 yen and wireless earphone with noise canceling function of 52% off, etc.](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/9/c88341f90bab7fe3ce1dc78d8bd6b02d_0.jpeg)